|
I am a PhD student in Computer Engineering at University of Waterloo. In my research, I work on security and privacy of computer systems. I am fortunate to be advised by Prof. Mahesh Tripunitara. In my master's I was advised by Prof. Mahesh Tripunitara and Prof. Werner Dietl. Before graduate school, I completed by undergraduate studies in Electrical Engineering at University of Waterloo. Prior to graduate school, I interned at Amazon in the search experience team and also worked there for 1 year contributing to the labor scheduling team. Outside of work, I enjoy reading, photography and running. Email / CV / LinkedIn / Google Scholar |

|
|
My research interests lie in computer security, algorithms and program analysis. In my undergraduate studies, I had the opportunity to work with Prof. Mahesh Tripunitara on a research project of understanding the semantics of access control lists in open source implementation of lightweight directory access protocol. I contributed to the project by coming up with an efficient way to determining the access control matrix, comparing it with the existing solutions. |
|
Paper with Boyun Zhang, Nelu Mihai and Mahesh Tripunitara was awarded "Best Student Paper" at the Second International Symposium on Emerging Information Security and Applications (EISA), 2021. |
|
|
|
|
|
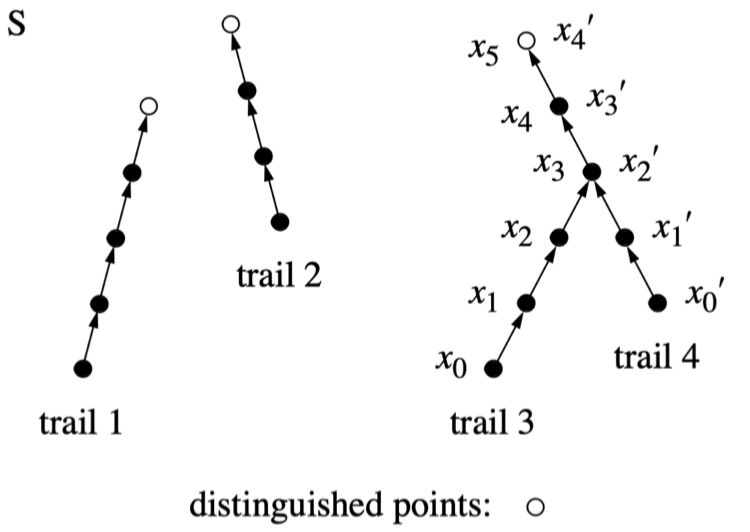
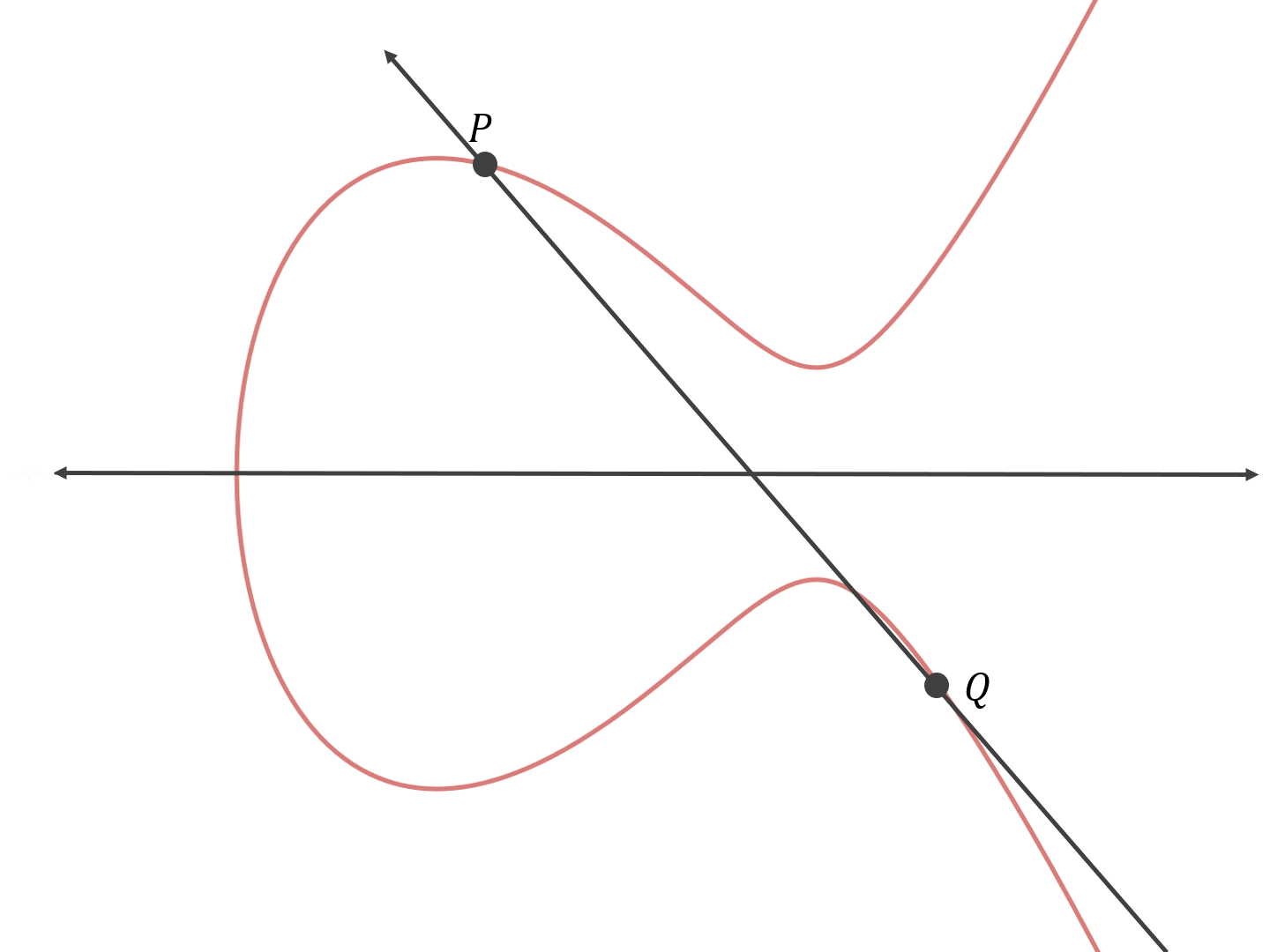
There are many applications of collision search algorithms in cryptanalysis. These may involve searching the space of keys, plaintext or ciphertext. For public key cryptosystems, they may be aimed at solving difficult mathematical problems such as computing factorization and discrete logarithms. In the paper, Parallel Collision Search with Cryptanalytic Applications, Oorschot and Weiner present an efficient method to parallelize Pollard's rho and lambda methods for computing discrete logarithms in cyclic groups. This analysis can also be extended to efficiently computing the elliptic curve discrete logarithm problem over a finite field Ζp Report | Shank's Algorithm | Pollard's Rho Method | Pollard's Lambda Method |
|
|
 |
Trained machine learning models to detect malicious TLS certificates.
|
 |
Worked in the flexible labor scheduling team, responsible for working on an integer linear programming problem constituting developing weekly schedules for over 30000 associates accross the globe. |
|
Worked on implementing a recommendation strategy service for Amazon's search results. |
|
|